FIXING THE INTERNET ROUTING SYSTEM
INTERNET ROUTING ISSUES
The issues with BGP have been understood for many years, and the Internet industry has attempted to develop a number of solutions, but these have been slow to be adopted and do not currently offer a complete fix.
Gaps in routing security

Lack of path selection, control & validation

Challenges in enforcing data sovereignty

SCION, built on trust for today’s needs
MORE Security
In today’s Internet, users need to be able to trust the networks to which they are sending their data and the networks through which their data passes. SCION has been designed with security considerations at the forefront, introducing the concept of trusted networks and domains combined with robust verification to address the existing issues with how data is sent over the Internet.
MORE Reliability
SCION can use existing Internet infrastructure but offers fast multi-path discovery and path selection. Users can select how their data is sent to other SCION networks, as applications are able to choose paths based on optimal characteristics or other parameters. Applications can also very quickly switch (within 1 or 2 seconds) to alternative paths in the event of link failure, congestion, or denial-of-service attacks, providing higher levels of assurance of availability and reliability.

SCION advantages
Trusted networks for reduced attack surface
Path validation against route leaks and spoofing
Geofencing for data sovereignty
Multi-path and fast fail-over for network uptime
Scalable and interoperable for easy deployment
SCION is based on Internet protocols and can utilize existing Internet infrastructure. No change is needed to the internal network infrastructure of a network operator, and devices that are not SCION enabled can utilize SCION gateways.
The aim is to have the SCION technology recognised as an IETF standard, and several Internet Drafts describing the various aspects have been published and are currently progressing through the IETF with a view to being published as RFCs.
SCION FEATURES: HOW SCION WORKS
SCION addresses many of the existing issues with how data is sent over the Internet, including those relating to inter-domain routing security and path selection. It introduces the concept of trusted networks and domains, and supports fast multi-path discovery and failover between participating networks.

Trust model based on Isolation Domains (ISDs)
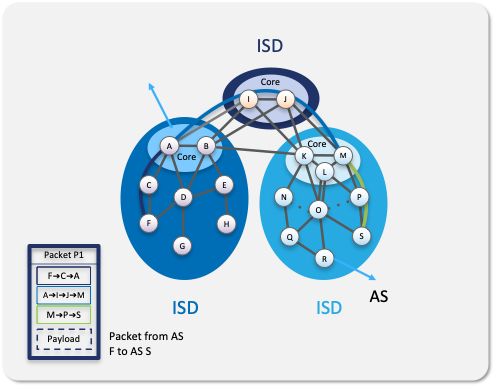
The SCION trust model is based around Isolation Domains (ISDs) that are logical groupings of participating networks (ASes) sharing a uniform trust environment – namely a common jurisdiction with agreed trust policies. Each ISD is administered by one or more core ASes who collectively generate a trust root called the Trust Root Configuration (a collection of X.509 certificates with ISD information). This is used to establish a standalone CA (i.e. one that is not reliant on third-party CAs) to issue certificates to each AS in the ISD, which can then be validated by the SCION Control Plane. It allows operators and users to establish and manage their own trust criteria and choose with whom to send, receive and transit traffic.
Control plane
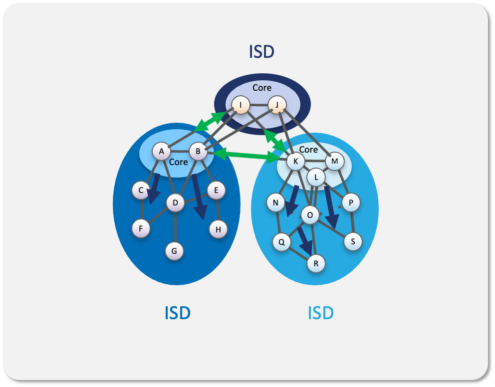
SCION utilizes a beaconing mechanism to discover path segments between ASes, which are then assembled into available routing paths that are cryptographically validated using the certificates issued to each AS in an ISD. It is necessary for each ASN in an ISD to run control plane services that include beaconing, path mapping and certificate/key management, and are typically provided by dedicated hardware or run in a Docker container.
By grouping ASes into ISDs, this also isolates their control planes and reduces communications overhead with the rest of the Internet. In addition, only explicitly allowed traffic is exchanged between ISDs.
Routing
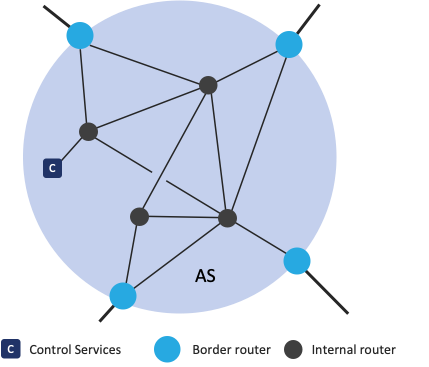
SCION sends data from network-to-network using simplified routers that are set-up on the borders of an AS, without changes being needed to the internal structure of that AS. These SCION-enabled routers peer with other SCION-enabled routers to forward and receive customer traffic and do not need to undertake control plane operations which are handled by the control services for each ISD. Endpoints can either run a SCION-aware stack or alternatively utilize a SCION gateway.
Download technical resources

SCION Technical DEEP DIVE

BOOK: The Complete Guide to SCION (2022)

SCION overview @ IETF
Frequently asked questions
How can SCION be deployed on the Internet?
SCION can be incrementally deployed at ISPs, who can make use of SCION’s features to route traffic through the backbone of the Internet. This is done by (transparently to end-users) encapsulating SCION packets inside IP packets. At the edges, encapsulation is removed and SCION packets are routed as usual. If a SCION path exists between two or more SCION-enabled ISPs, encapsulation is not needed.
Which ports does SCION run on?
The SCION protocol can be encapsulated on top of UDP. For more details, see the developer docs: https://docs.scion.org/en/latest/manuals/router.html#port-table.
What is the operating system that SCION runs on?
Why use ISDs? Shouldn't the Internet be a globally-connected entity?
Is SCION a source-routed architecture? What are differences with segment routing?
Does SCION need flow state to be set up on intermediate routers before communication can occur?
How is SCION overcoming configuration errors? Is this simply an artifact of the isolation property (one AS's errors don't impact others) or the reduction in configuration complexity?
How is SCION's multi-path routing concealing link failures from applications? A loss of some packets on a path will still introduce delays and retransmissions.
Does SCION work for hosts behind NATs?
How does SCION Interoperate with the existing Internet?
Does SCION replace existing Internet protocols?
Does SCION support IPv6?
What network layer(s) does SCION operate at?
What hardware and software is needed to run SCION?
SCION routing does not require specialized hardware, therefore it runs on commercial off-the shelf hardware or in virtualized platforms.
Is SCION standardized?
There is ongoing work at the IETF and at the Association’s Standardization Committee.
WE’RE HAPPY TO SHARE OUR INSIGHTS AT INDUSTRY EVENTS
If you’re interested in having us present SCION, don’t hesitate to reach out to us.